We all love using Facebook to connect with people, read articles, and see pictures of friends and family. What if you are looking for a friend of yours that you have not seen in years, and come across a Facebook page that you believe is your friend’s but in reality has been created by a scammer?
Scammers are using a tactic called ‘Profile cloning’. The tactic has been around for several years but is becoming more prevalent in 2016. It has become a serious security threat. Scammers have recently been targeting people over the age of 50, the majority being women.
Many people whose Facebook page has been cloned are claiming to friends that they have been “hacked” however this term is not completely accurate. The scammer has not logged into Facebook with your user name and password or taken over your account. They have simply taken public information, your profile picture and name, and created a new profile with that same information. The original profile created on Facebook has not been compromised.
When the scammer creates the new profile, they will send friend requests to everyone you are friends with already. Your friends may think nothing of the new profile and accept a friend request without a second thought.
When scammers clone a Facebook profile, what are they hoping to accomplish?
They want to use your Friends list to send them private messages in order to try to scam them.
Here are some examples of scams they use:
- They use Advance Fee Lottery Scams in order to lure victims into believing they have won an international lottery. Because the victim has won a large sum of money, the person sending you the messages requires a driver’s license, passport, and or your banking information in order to send you the money you are owed.
- They claim that you are stranded out of the country and need a short term loan to help you get back to the United States. The recipients think they are talking to the person they know and may agree to loan the person money so that they can get home.
- The scammer may pretend to be your friend in order to get a large amount of personal or financial information from you.
What to do if you or someone you know has had their Facebook profile cloned:
If it’s a friend double check to see if they have created a second profile before proceeding. If the person tells you they have not created a second account, report the profile to Facebook as someone who is impersonating you or your friend.
To report a cloned profile to Facebook:
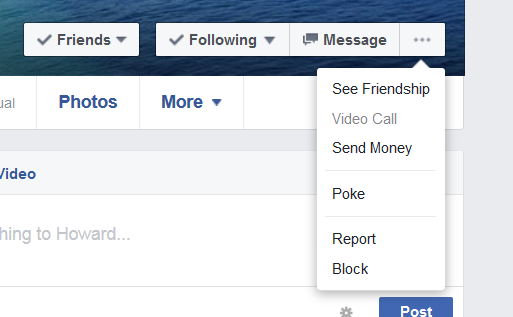
- Go to the cloned profile page.
- Click the 3 dots (…) next to the Message button.
- Click Report.
- Click Report this Profile.
- Click They’re pretending to be me or someone I know.
- Next click Report to Facebook.
- Post on your timeline (or tell your friend to) that you have been cloned and tag the people who have added the scammer as a friend. Include a link to the cloned profile in your post. Once Facebook has deleted the cloned profile, they will also delete your post with the cloned profile link in it so don’t be alarmed when the post disappears.
How to help prevent this from happening:
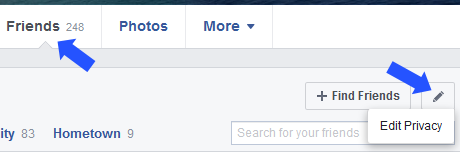
- Keep your Friends private. If they can’t spam your friends they have no reason to clone your profile. On your page click on Friends. Click the pen icon (manage). Click Edit Privacy. Under “Who can see your friend’s list”, select Friends.
- Don’t Friend anyone who you aren’t already familiar with.
You may want to search for your name on Facebook in the city which you live in. Just to make sure this hasn’t happened to you already. It’s possible you’ll find other people with your name, just make sure they don’t have your picture and other information as well.
Happy Facebooking!







 Hello XP users,
Hello XP users,